Today 1 in 5 consumer PCs is a Mac so they are a tasty target for hackers, spammers and criminals.
See these two brief videos for more info: Do Macs get viruses?
and this: What does a Mac threat look like?
Thursday, November 4, 2010
Wednesday, November 3, 2010
Free Anti virus protection for Macs
Introducing Sophos Anti-Virus for Mac Home Edition
Sophos has released their latest free tool - Sophos Anti-Virus for Mac Home Edition. This is their first consumer anti-malware product designed to provide Mac home users with up–to-the-hour protection that is simple to use and FREE!
Sophos Anti-Virus for Mac Home Edition features:
• Full protection from viruses, Trojans and worms— both Mac and Windows threats
• Anti-virus technology that stops all threats in their tracks, even if it’s something new
• Quarantine and cleanup of threats it finds
• Business-quality anti-virus, backed by SophosLabs
• Protection that is light on resources and easy to use - it installs quickly and doesn’t get in your way
• And yes, it’s 100%, totally, absolutely, completely free
Sophos Anti-Virus for Mac Home Edition is available for Mac OSX 10.4 (Tiger), 10.5 (Leopard) or 10.6 (Snow Leopard), and supports all Apple Mac hardware including the new MacBook Air.
To downlad it free, go to www.sophos.com/products/free-tools/free-mac-anti-virus/
B Technologies is a Gold partner of Sophos so far any security needs, write to us at info@btechnologies.com and we will get back to you promptly.
Sophos has released their latest free tool - Sophos Anti-Virus for Mac Home Edition. This is their first consumer anti-malware product designed to provide Mac home users with up–to-the-hour protection that is simple to use and FREE!
Sophos Anti-Virus for Mac Home Edition features:
• Full protection from viruses, Trojans and worms— both Mac and Windows threats
• Anti-virus technology that stops all threats in their tracks, even if it’s something new
• Quarantine and cleanup of threats it finds
• Business-quality anti-virus, backed by SophosLabs
• Protection that is light on resources and easy to use - it installs quickly and doesn’t get in your way
• And yes, it’s 100%, totally, absolutely, completely free
Sophos Anti-Virus for Mac Home Edition is available for Mac OSX 10.4 (Tiger), 10.5 (Leopard) or 10.6 (Snow Leopard), and supports all Apple Mac hardware including the new MacBook Air.
To downlad it free, go to www.sophos.com/products/free-tools/free-mac-anti-virus/
B Technologies is a Gold partner of Sophos so far any security needs, write to us at info@btechnologies.com and we will get back to you promptly.
Labels:
anti-virus,
free service,
great service,
security,
spyware,
virus protection
Thursday, June 10, 2010
World Cup 2010 - be aware of the scams!
Our close friends at Sophos - the IT security experts sent us this link to important information regarding scams that appear around World Cup 2010 time that you or someone you know may be exposed to.
People who usually have little or no interest in soccer may turn into soccer fiends when the world Cup starts.
And if you can change your behaviour -- quite innocently -- in "real life" because the World Cup is on, you run the risk of changing your behaviour online -- to your own risk -- at the same time.
Clicking dodgy links, running to five different little-known websites to compare odds, checking who's playing whom and when, trying to find crowd-shot video of dodgy refereeing decisions, looking up historical data to prove England really are rubbish, and more.
If you want to be prepared, read this:
http://www.sophos.com/blogs/duck/g/2010/06/10/world-cup-2010-scam-odds
People who usually have little or no interest in soccer may turn into soccer fiends when the world Cup starts.
And if you can change your behaviour -- quite innocently -- in "real life" because the World Cup is on, you run the risk of changing your behaviour online -- to your own risk -- at the same time.
Clicking dodgy links, running to five different little-known websites to compare odds, checking who's playing whom and when, trying to find crowd-shot video of dodgy refereeing decisions, looking up historical data to prove England really are rubbish, and more.
If you want to be prepared, read this:
http://www.sophos.com/blogs/duck/g/2010/06/10/world-cup-2010-scam-odds
Labels:
anti-virus,
computer tips,
Interesting,
internet,
Internet use,
privacy,
security,
virus protection
Tuesday, June 1, 2010
Do you need to know your internet IP address?
There are a number of reasons why you might need to find your internet IP address and it only takes a few seconds to do.
Go to:
http://www.whatsmyip.org/
and when you arrive on the site your IP address will be prominently displayed on the top of the page.
Simple as that.
Go to:
http://www.whatsmyip.org/
and when you arrive on the site your IP address will be prominently displayed on the top of the page.
Simple as that.
Labels:
computer tips,
free service,
internet,
Internet use
5 tips to help keep your passwords secret
Treat your passwords with as much care as you treat the information that they protect.
Use strong passwords to log on to your computer and to any site where you enter your credit card number, or any financial or personal information—including social networking sites.
1. Never provide your password over e-mail or in response to an e-mail request.
2. Internet "phishing" scams use fraudulent e-mail messages to entice you to reveal your user names and passwords, steal your identity, and more.
3. Do not type passwords on computers that you do not control
• Computers such as those in Internet cafes, computer labs, kiosk systems, conferences, and airport lounges should be considered unsafe for any personal use other than anonymous Internet browsing.
• Cyber criminals can purchase keystroke logging devices which gather information typed on a computer, including passwords.
4. Don't reveal passwords to others
• Keep your passwords hidden from friends or family members (especially children) who could pass them on to other, less trustworthy individuals.
5. Protect any recorded passwords
• Don't store passwords on a file in your computer, because criminals will look there first.
• Keep your record of the passwords you use in a safe, secure place.
6. Use more than one password
• Use different passwords for different Web sites and services.
Use strong passwords to log on to your computer and to any site where you enter your credit card number, or any financial or personal information—including social networking sites.
1. Never provide your password over e-mail or in response to an e-mail request.
2. Internet "phishing" scams use fraudulent e-mail messages to entice you to reveal your user names and passwords, steal your identity, and more.
3. Do not type passwords on computers that you do not control
• Computers such as those in Internet cafes, computer labs, kiosk systems, conferences, and airport lounges should be considered unsafe for any personal use other than anonymous Internet browsing.
• Cyber criminals can purchase keystroke logging devices which gather information typed on a computer, including passwords.
4. Don't reveal passwords to others
• Keep your passwords hidden from friends or family members (especially children) who could pass them on to other, less trustworthy individuals.
5. Protect any recorded passwords
• Don't store passwords on a file in your computer, because criminals will look there first.
• Keep your record of the passwords you use in a safe, secure place.
6. Use more than one password
• Use different passwords for different Web sites and services.
Labels:
computer tips,
Internet use,
privacy,
security,
useful
Monday, May 31, 2010
How strong is YOUR password?
Test your password with a password checker
Are you wondering if the password you created is good enough?
A password checker evaluates your password's strength automatically.
Click on the following link if you want to check your password's strength:
https://www.microsoft.com/protect/fraud/passwords/checker.aspx?WT.mc_id=Site_Link
Are you wondering if the password you created is good enough?
A password checker evaluates your password's strength automatically.
Click on the following link if you want to check your password's strength:
https://www.microsoft.com/protect/fraud/passwords/checker.aspx?WT.mc_id=Site_Link
Labels:
computer tips,
Internet use,
privacy,
security,
useful
How to Create Strong Passwords
Strong passwords are an important protection to help you protect your data.
Keys to password strength: length and complexity
An ideal password is long and has letters, punctuation, symbols, and numbers.
• Whenever possible, use at least 8 characters or more.
• The greater the variety of characters in your password, the better.
• Use the entire keyboard, not just the letters and characters you use or see most often.
Create a strong password you can remember
There are many ways to create a long, complex password. Here is one way that may make remembering it easier:
Start with a sentence or two (about 10 words total). Think of something meaningful to you.
For example take he following sentence:
"Long and complex passwords are safest. I keep mine secret." (10 words)
Turn this sentences into a row of letters. Use the first letter of each word.
= lacpasikms (10 characters)
Add complexity. Make only the letters in the first half of the alphabet uppercase.
= lACpAsIKMs (10 characters)
Add length with numbers. Put two numbers that are meaningful to you between the two sentences.
= lACpAs56IKMs (12 characters)
Add length with punctuation. Put a punctuation mark at the beginning.
= ?lACpAs56IKMs (13 characters)
Add length with symbols. Put a symbol at the end.
= ?lACpAs56IKMs" (14 characters)
Common password pitfalls to avoid
Cyber criminals use sophisticated tools that can rapidly decipher passwords.
Avoid creating passwords using:
• Dictionary words in any language.
Words in all languages are vulnerable.
• Words spelled backwards, common misspellings, and abbreviations.
• Sequences or repeated characters.
Examples: 12345678, 222222, abcdefg, or adjacent letters on your keyboard (qwerty).
• Personal information.
Your name, birthday, driver's license, passport number, or similar information.
Protect your passwords from prying eyes
The easiest way to "remember" passwords is to write them down.
It is okay to write passwords down, but keep them secure.
Keys to password strength: length and complexity
An ideal password is long and has letters, punctuation, symbols, and numbers.
• Whenever possible, use at least 8 characters or more.
• The greater the variety of characters in your password, the better.
• Use the entire keyboard, not just the letters and characters you use or see most often.
Create a strong password you can remember
There are many ways to create a long, complex password. Here is one way that may make remembering it easier:
Start with a sentence or two (about 10 words total). Think of something meaningful to you.
For example take he following sentence:
"Long and complex passwords are safest. I keep mine secret." (10 words)
Turn this sentences into a row of letters. Use the first letter of each word.
= lacpasikms (10 characters)
Add complexity. Make only the letters in the first half of the alphabet uppercase.
= lACpAsIKMs (10 characters)
Add length with numbers. Put two numbers that are meaningful to you between the two sentences.
= lACpAs56IKMs (12 characters)
Add length with punctuation. Put a punctuation mark at the beginning.
= ?lACpAs56IKMs (13 characters)
Add length with symbols. Put a symbol at the end.
= ?lACpAs56IKMs" (14 characters)
Common password pitfalls to avoid
Cyber criminals use sophisticated tools that can rapidly decipher passwords.
Avoid creating passwords using:
• Dictionary words in any language.
Words in all languages are vulnerable.
• Words spelled backwards, common misspellings, and abbreviations.
• Sequences or repeated characters.
Examples: 12345678, 222222, abcdefg, or adjacent letters on your keyboard (qwerty).
• Personal information.
Your name, birthday, driver's license, passport number, or similar information.
Protect your passwords from prying eyes
The easiest way to "remember" passwords is to write them down.
It is okay to write passwords down, but keep them secure.
Labels:
computer tips,
Internet use,
privacy,
security,
useful
Monday, March 1, 2010
Make long URL addresses usable!
Have you ever sent someone a huge url (address) to a website and wished it didn't look quiet as complicated?
Here is a fantastic tool called Tiny URL which is available free of charge to anybody and is very easy to use, that turns big urls into short ones. Here is an example of how it works:
You can turn this URL:
Here is a fantastic tool called Tiny URL which is available free of charge to anybody and is very easy to use, that turns big urls into short ones. Here is an example of how it works:
You can turn this URL:
http://rover.ebay.com/rover/1/711-53200-19255-0/1?tinto this tinyURL:
ype=3&campid=5336224516&toolid=10001&customid=tiny-
hp&ext=unicycle&satitle=unicycle
http://tinyurl.com/unicyclesWhich one would you rather cut and paste into your browser? That's the power of TinyURL!
Labels:
computer tips,
free service,
great service,
Interesting,
Shortcuts,
useful
SCAMS - Learn All About Them
Too many businesses become victims of online and offline scams. There is a handy booklet published by the government that you are able to download for free and learn more about the scams, how they work and how you can defend against them.
The link is as follows:
http://www.accc.gov.au/content/index.phtml/tag/TheLittleBlackBookOfScams08
This is what the website says about the booklet:
The little black book of scams highlights a variety of popular scams that regularly target Australian consumers and small business in areas such as fake lotteries, internet shopping, mobile phones, online banking, employment and investment opportunities. It also offers consumers tips on how to protect themselves from scams, what they can do to minimise damage if they do get scammed and how they can report a scam.
The link is as follows:
http://www.accc.gov.au/content/index.phtml/tag/TheLittleBlackBookOfScams08
This is what the website says about the booklet:
The little black book of scams highlights a variety of popular scams that regularly target Australian consumers and small business in areas such as fake lotteries, internet shopping, mobile phones, online banking, employment and investment opportunities. It also offers consumers tips on how to protect themselves from scams, what they can do to minimise damage if they do get scammed and how they can report a scam.
Labels:
free service,
privacy,
security,
SPAM,
spyware,
useful,
virus protection
Thursday, February 4, 2010
Open any image format with ease
In our last post we told you about 2 great programs to use to open any video formats but we had a number of enquiries about viewing (and editing) some obscure image files images.
Go to http://www.download.com/ and download a free product called "Irfan View".
This small program will open / edit images in any file format that you throw at it.
This product has been downloaded a staggering 47 million times so you know it works!
It has other impressive editing function that you can explore yourself.
Go to http://www.download.com/ and download a free product called "Irfan View".
This small program will open / edit images in any file format that you throw at it.
This product has been downloaded a staggering 47 million times so you know it works!
It has other impressive editing function that you can explore yourself.
Play any video file with ease
Have you ever struggled to play a video file?
You now have two perfect options to solve this problem.
Go to http://www.download.com/ and download either one of these free products. Once you have installed them they will play 98% of any video formats you may have.
They are:
- GOM Media Player
- VLC Media Player
GOM for example plays formats including DAT, MPEG, DivX, XviD, WMV, ASF, AVI, and MOV, and common codecs like FLV1, AC3, OGG, MP4, and H263.
If you need confirmation that these products are trustworthy, you will see that both of them have been downloaded a staggering 20 million times!
They have some other impressive functions but you can explore them yourself.
As always, if you need any help or advice, just contact us on 1300 885 200 or at support@btechnologies.com
You now have two perfect options to solve this problem.
Go to http://www.download.com/ and download either one of these free products. Once you have installed them they will play 98% of any video formats you may have.
They are:
- GOM Media Player
- VLC Media Player
GOM for example plays formats including DAT, MPEG, DivX, XviD, WMV, ASF, AVI, and MOV, and common codecs like FLV1, AC3, OGG, MP4, and H263.
If you need confirmation that these products are trustworthy, you will see that both of them have been downloaded a staggering 20 million times!
They have some other impressive functions but you can explore them yourself.
As always, if you need any help or advice, just contact us on 1300 885 200 or at support@btechnologies.com
Monday, February 1, 2010
Information technology progresses faster than you think
This is a video follow up of the YouTube hit 'Shift Happens' with some fascinatings facts about the progression of information technology.
Labels:
B Technologies,
computer tips,
great idea,
Interesting,
useful
Wednesday, January 20, 2010
How to get rid of a common and current vicious virus
We are getting a lot of calls about a vicious virus that is getting through most of the popular anti virus programs.
As always, we have the answer so the way to deal with this is as follows:
1. Go to http://www.download.com/
2. In the search box on this site type Malwarebytes and click Search
3. In the list of search results, find Malwarebytes Anti-Malware (probably the first in the list)
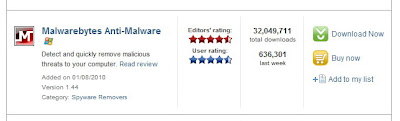
4. Click on Download now
5. In the following screen if the file download doesn’t automatically pop up, click on click here to try again
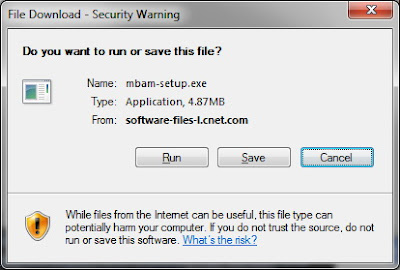
7. Once downloaded, go to your Desktop (or wherever you saved the file) and double-click mbam-setup.exe
8. Follow the prompts to install the software
9. Once installed, the software will place an icon on your Desktop, double-click this to start Malwarebytes Anti-Malware

10. Click on the Update tab and update the software
11. Once the software has been updated, restart your computer in Safe Mode. To do this, follow the steps below:
a. Restart your computer
b. When the screen goes black, and then your computer comes to life again, start slowly tapping on the F8 key – do not hold the key down, just tap tap tap on it until you see a menu appear with some startup options
c. Use the arrow keys on your keyboard to select Safe Mode and then press Enter. You may also then be asked which operating system to start. Generally, there is only one but if not, choose the one with the problem from the list and press Enter
d. If you have a login screen, login to your computer as normal (you may have to log on as the Administrator user)
e. When you see a warning for safe mode, click Yes
12. Double-click the icon on the desktop for Malwarebytes Anti-Malware
13. Click the button to perform a Full Scan
14. When the scan is complete, remove all threats found
15. Exit Malwarebytes Anti-Malware and perform a full scan using your up-to-date anti-virus software. If you don’t have an up-to-date anti-virus software, you should get one as soon as possible to prevent any further viruses.
16. Restart your computer in normal mode and hopefully the threat has been removed.
For tips on how to avoid viruses, see our earlier post here: http://btechnologies.blogspot.com/2009/02/protect-yourself-from-dangerous-virus.html
As always, we have the answer so the way to deal with this is as follows:
1. Go to http://www.download.com/
2. In the search box on this site type Malwarebytes and click Search
3. In the list of search results, find Malwarebytes Anti-Malware (probably the first in the list)

4. Click on Download now
5. In the following screen if the file download doesn’t automatically pop up, click on click here to try again

7. Once downloaded, go to your Desktop (or wherever you saved the file) and double-click mbam-setup.exe
8. Follow the prompts to install the software
9. Once installed, the software will place an icon on your Desktop, double-click this to start Malwarebytes Anti-Malware

10. Click on the Update tab and update the software
11. Once the software has been updated, restart your computer in Safe Mode. To do this, follow the steps below:
a. Restart your computer
b. When the screen goes black, and then your computer comes to life again, start slowly tapping on the F8 key – do not hold the key down, just tap tap tap on it until you see a menu appear with some startup options
c. Use the arrow keys on your keyboard to select Safe Mode and then press Enter. You may also then be asked which operating system to start. Generally, there is only one but if not, choose the one with the problem from the list and press Enter
d. If you have a login screen, login to your computer as normal (you may have to log on as the Administrator user)
e. When you see a warning for safe mode, click Yes
12. Double-click the icon on the desktop for Malwarebytes Anti-Malware
13. Click the button to perform a Full Scan
14. When the scan is complete, remove all threats found
15. Exit Malwarebytes Anti-Malware and perform a full scan using your up-to-date anti-virus software. If you don’t have an up-to-date anti-virus software, you should get one as soon as possible to prevent any further viruses.
16. Restart your computer in normal mode and hopefully the threat has been removed.
Labels:
anti-virus,
spyware,
useful,
virus protection
Subscribe to:
Posts (Atom)




